Cybersecurity Identify
- Asset Management
Continuously identify your organization’s IT assets in real-time, including determining gaps or other potential security risks that could harm your assets.
-
Business Environment
Accurately identify your organization’s ability to determine cybersecurity roles and responsibilities. Make risk-management decisions with an adequate, accurate understanding of priorities of the appropriate objectives.
- Security Governance
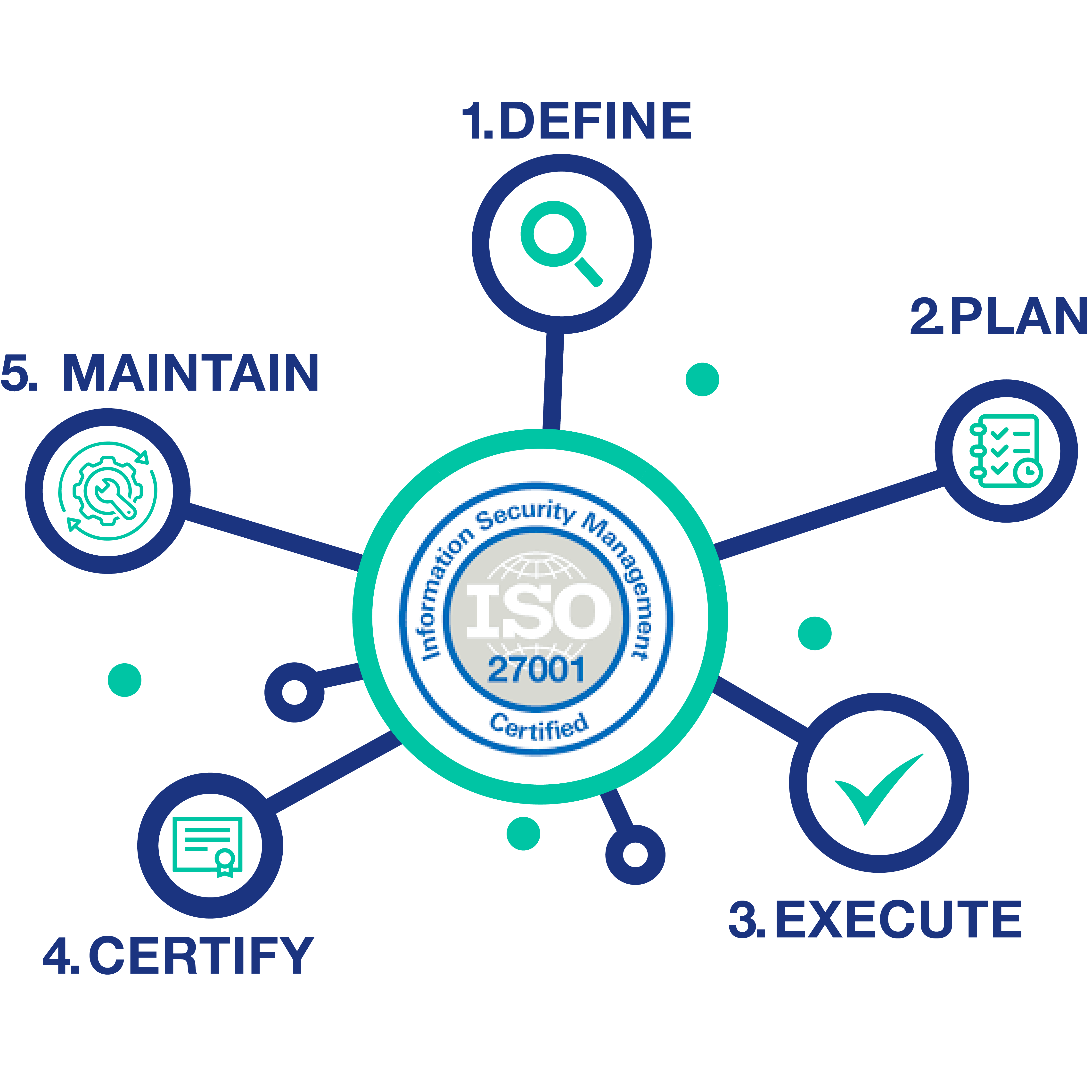
Get an advanced structured framework for establishing an efficient Information Security Management System (ISMS) for your organization. Trusted Chain applies your security procedures and policies through a certification audit for ISO 27001.
- Risk Assessment
Identify diverse hardware and software IT assets and risk potentials from a cyberattack.
- Management Strategy
Identify potential risks that may threaten your organization. Prioritize and plan defenses, then apply a comprehensive strategy to avoid those risk
Cybersecurity Detection
- Continuous Security Monitoring
At Trusted Chain, the ultimate center of your security, the Security Operations Center (SOC) is run and managed by a professional cybersecurity analysis team. Continuous Security Monitoring is provided by most modern detection systems and smart monitoring resources.
Comprehensive Assessment
Through our inclusive, innovative Trust Chain methodology, we can accurately evaluate your company’s resilience and identify any vulnerabilities in your resources: physical servers and hardware, networks, smart devices, operating systems, and software.
- Detection Processes
Implement a collection of cybersecurity tests: Penetration Test, Phishing & Vishing Test, DDOS Stress Test, and more. Simulate actual scenario hacker attacks to get an in-depth evaluation that uncovers invisible security gaps.
- Anomalies and Events
Real-time detection of anomalies and abnormal changes in your network’s standard communication. An anomaly can result from malware or cyberattacks or other faults and hardware failures.
- Security Analyses
Have any security information you need and real-time enlightened views. Receive the latest alerts via the in-house SIEM security system.
Cyber Protection
- Comprehensive Information Protection Procedures
Get complete all-in-one protection for your resources: servers, workstations, networks, mobiles, devices, etc. Enjoy safe and secure computing environments utilizing the most modern Artificial Intelligence-based security software and global cloud security solutions for antiviruses and next-generation firewalls and shields.
- Database Protection
Your customers’ information is usually sensitive and personal. Don’t take chances with their data. Take the solid protection of ZeroTrust, featuring next-generation firewalls. Trusted Chain Shields is also structured according to Gartner Inc to secure your business against any OWASP, Botnet, and Layer 7 DDoS.
- Access Control Protection
Secure your resource access without more complex passwords. Implement the resilience and agility of the latest identity solutions like Two Factor Authentication.
- Maintenance Protective Technology
Periodically check all installation elements like cameras, detectors, computers, circuits, etc., for ongoing maintenance and to confirm they are functioning correctly.
- Maintenance Protective Technology
Checking periodically of all installation elements like cameras, detectors, computers, circuits, etc. To validate its function and to maintain them.
- Maintenance Protective Technology
Checking periodically of all installation elements like cameras, detectors, computers, circuits, etc. To validate its function and to maintain them.
- Real-Time Security Assessment
Always stay informed of your organization’s current security status and vulnerabilities. Make your security decisions based on the latest updates and according to global cybersecurity standards.
- Advanced Training and Awareness
Level up your IT team’s security skills with certified training courses. Let your employees increase their sense of security awareness for better compliance. Trusted Chain simplified education materials are sophisticated yet designed for the non-tech audience to keep them informed of the latest developments
- Maintenance Protective Technology
Checking periodically of all installation elements like cameras, detectors, computers, circuits, etc. To validate its function and to maintain them.
- Real-Time Security Assessment
Always stay informed of your organization’s current security status and vulnerabilities. Make your security decisions based on the latest updates and according to global cybersecurity standards.
- Advanced Training and Awareness
Level up your IT team’s security skills with certified training courses. Let your employees increase their sense of security awareness for better compliance. Trusted Chain simplified education materials are sophisticated yet designed for the non-tech audience to keep them informed of the latest developments
Cybersecurity Recover and Response
- Response Planning
Planning complete instructions for responding immediately is critical to rescue systems and helps support a faster recovery. Trusted Chain experts are available 24/7 as firefighters. In addition, Trusted Chain offers complete business assessments.
- Forensics Communications Analysis
If any security breach occurs, complete a full certified forensic and communications analysis to decide legally which party takes responsibility, including all your company devices and networks.

- Recovery Planning
Define each incident management role to develop a Disaster Recovery Plan (DRP) and a Business Continuity Plan (BCP) according to Crisis Management Strategy best practices. Recovery Planning finds quick alternative resources and redirects them into restoring data and information systems following a disaster.
- Mitigation Improvements
Apply incident mitigation plans, and procedures like constantly updating devices and software. Repeatedly ensure that every standard is appropriately applied.
